When considering the different types of Multifactor Authentication (MFA) it is clear that many could be a challenge for students with a wide range of disabilities. However, when you add the use of assistive technologies and customisation or potential personalisation the barriers begin to come down. That is as long as the actual website or app hosting the required verification of a sign up or log in is accessible.
With these caveats in place it seemed that as long as students were provided with at least three or more choices it would be possible to navigate MFA. That thought led to a mini survey of around a third of the universities in UK to see what was on offer.
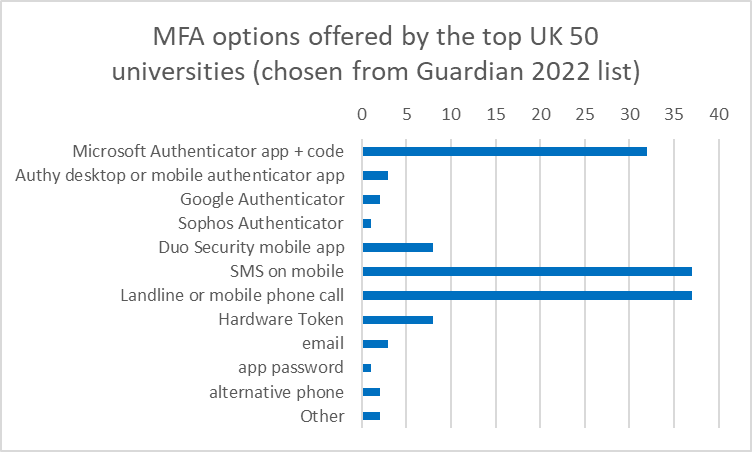
Several universities offer a password as their main login method and then additional security for certain more sensitive areas. 42 out of 50 universities offer apps, but only two apppear to provide 2 options for the type of app, such as Microsoft and Authy on a desktop, which can be very helpful for assistive technology users who do not have smart phones or find their desktop AT easier to use. 8 universities offer hardware tokens and 6 offer at least 5 options but 9 had no alternatives that could be easily found and 14 universities made searching for support difficult by not having easy to reach information pages.
Microsoft authentication app, a text message to a mobile phone or a call to either a landline or mobile, were the most common verification methods after a login email and password had been generated.
So in summary…
- many students have limited options if they do not want to or could not use the Microsoft Authentication app or do not have a smart phone.
- there are rarely more than two options if using an app is not possible and one includes the use of a landline, which may not always be possible in a college or university setting
- it often took more than ‘three clicks’ or selection choices to reach any supporting materials and these rarely mentioned the use of assistive technologies. However, there was usually a contact form or email address available.



